Blog
Security
/ 16 Jan, 2026Scattered Spider Tradecraft: Identity Abuse, Attack Flow, and Defense
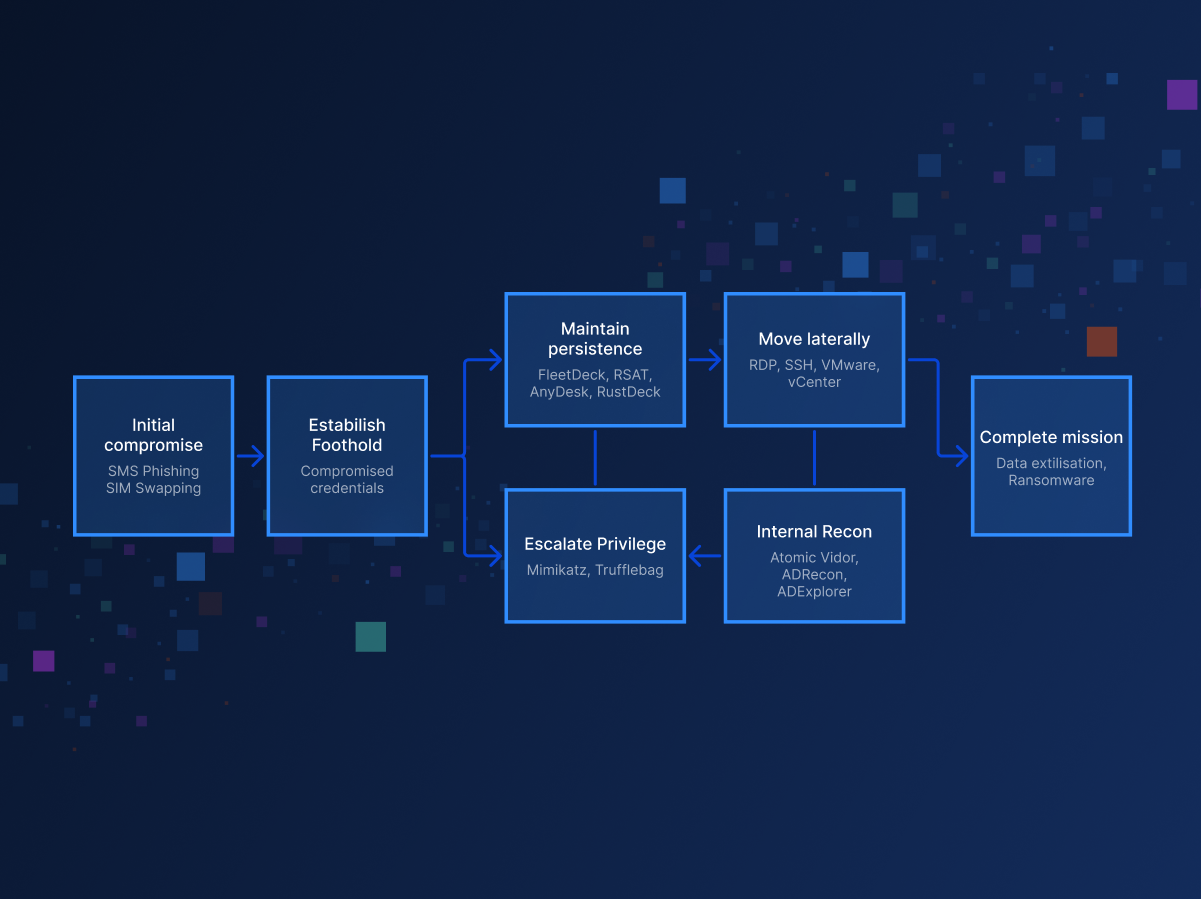
Scattered Spider is a highly adaptive cybercrime group that breaches enterprises by abusing identity, trust, and legitimate access paths rather than malware exploits.
Learn about their identity-centric attack flow, real-world campaigns like the MGM and Caesars breaches, and how to defend against these sophisticated threats.
Security
/ 16 Jan, 2026Scattered Spider Tradecraft: Identity Abuse, Attack Flow, and Defense
Scattered Spider is a highly adaptive cybercrime group that breaches enterprises by abusing identity, trust, and legitimate access paths rather than malware exploits.
Learn about their identity-centric attack flow, real-world campaigns like the MGM and Caesars breaches, and how to defend against these sophisticated threats.

New Feature
/ 23 Oct, 2023OAuth 2.0 Fine-Grained API Authorization with Gate and OpenAPI
Protect your API against unauthorized access without changing your application.
Our newest Gate plugin automatically enforces OpenAPI security checks, so you can implement fine-grained access control for your APIs and workloads without writing any extra code.

Tutorial
/ 16 Oct, 2023Rate Limiting for Large-scale, Distributed Applications and APIs Using GCRA
Rate limiting is a key defense against bots and threats for APIs and backends. Traditional IP-based rate limiting techniques are insufficient today because they can be easily bypassed.
In this article, we discuss the state of the art when it comes to rate limiting and how we have implemented a modern, distributed, identity-based rate limiting plugin for Gate.

Tutorial
/ 10 Oct, 2023Context-aware authentication: fight identity fraud and qualify your users
Knowing your users is becoming increasingly important. Whether you're a B2B PLG business trying to convert leads or a fintech business fending off attacks, it's essential to have more context about who is accessing your platform and to customize your behavior accordingly.
In this article, we show how you can leverage SlashID's webhooks to enrich the authentication context, customize the user journey, block malicious users.

Deep Dives
/ 28 Sep, 2023Backend Authentication and Authorization Patterns: Benefits and Pitfalls of Each
Identity in distributed applications is hard. In large and complex environments with multiple services, a number of patterns have emerged to authenticate and authorize traffic.
In this article, we’ll discuss the most common ones, how to implement them, and their pros and cons.

Deep Dives
/ 21 Sep, 2023JWT Implementation Pitfalls, Security Threats, and Our Approach to Mitigate Them
JSON Web Tokens (JWTs) are one of the most common ways to transfer identity claims and prove the identity of a user or an entity. JWTs have become very popular in recent years because they are easy to use, read, and debug.
JWTs provide a lot of flexibility at the expense of several security risks that are often overlooked. In this article, we'll discuss common risks when implementing or manipulating JWTs and our approach to avoiding them.

Tutorial
/ 18 Sep, 2023No-code anti-phishing protection of internal apps with Passkeys
Phishing is one of the most common causes of data breaches. According to Verizon's DBIR report, over 50% of incidents start with phishing or stolen credentials. WebAuthn/Passkeys are an effective way to stop phishing and credential stealing attempts on their tracks.
In this article, we’ll show how you can use Gate to enforce Passkeys authentication for users without modifying the application code.

Tutorial
/ 14 Sep, 2023Firewalling OpenAI APIs: Data loss prevention and identity access control
Large Language Models (LLMs) have taken the world by storm, and they are now used for many tasks by consumers and enterprises alike. However, the risk of accidentally disclosing sensitive data to the models is very high as the recent Samsung case shown.
In this article, we’ll show how you can use Gate to detect sensitive data in requests sent to the OpenAI APIs, as well as enforcing access control so that only users with certain roles can access the APIs.

New Feature
/ 12 Sep, 2023Ditch your organizations table
Suborgs make it effortless and secure to implement complex identity structures such as multi-tenancy B2B apps and multi sided marketplaces.


Tutorial
/ 5 Sep, 2023Protecting Exposed APIs: Avoid Data Leaks with SlashID Gate and OPA
Adequately protecting APIs is key to avoid data leaks and breaches.
Just recently, an exposed API allowed an attacker to scrape over 2.6 million records from Duolingo.
In this article, we’ll show how you can use Gate to detect, respond to, and prevent these kinds of incidents.


