Blog
Security
/ 16 Jan, 2026Scattered Spider Tradecraft: Identity Abuse, Attack Flow, and Defense
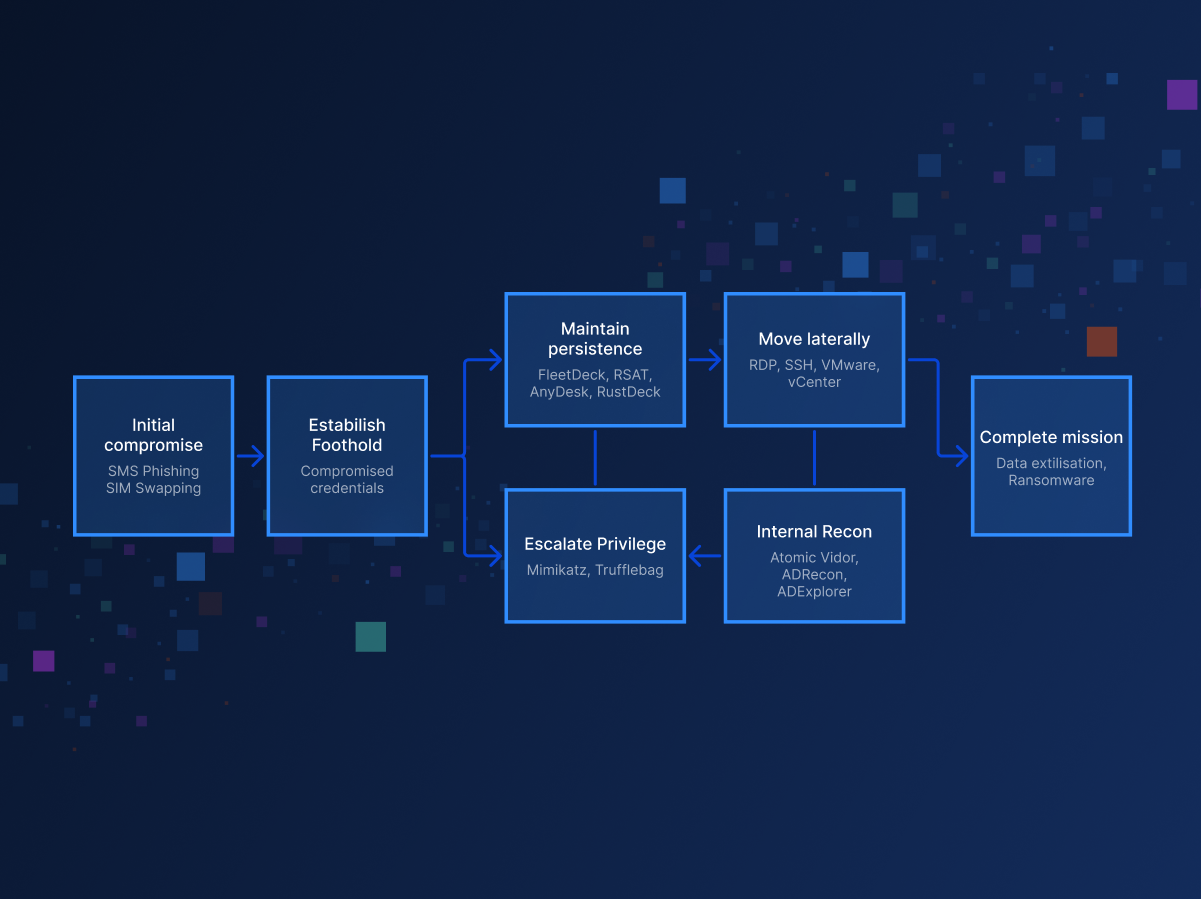
Scattered Spider is a highly adaptive cybercrime group that breaches enterprises by abusing identity, trust, and legitimate access paths rather than malware exploits.
Learn about their identity-centric attack flow, real-world campaigns like the MGM and Caesars breaches, and how to defend against these sophisticated threats.
Security
/ 16 Jan, 2026Scattered Spider Tradecraft: Identity Abuse, Attack Flow, and Defense
Scattered Spider is a highly adaptive cybercrime group that breaches enterprises by abusing identity, trust, and legitimate access paths rather than malware exploits.
Learn about their identity-centric attack flow, real-world campaigns like the MGM and Caesars breaches, and how to defend against these sophisticated threats.

Product Releases
/ 2 Apr, 2024SlashID SDK for PHP and Laravel authentication
While very popular, PHP lacks modern identity and access management (IAM) capabilities. SlashID changes that with the release of our SDK for PHP and Laravel.
This is just the beginning; according to W3Tech PHP is used by over 76% of indexed websites. In the weeks to come, we aim to cover other popular frameworks such as Drupal and Symfony.

Deep Dives
/ 6 Mar, 2024Adding custom claims to identity tokens
Adding custom claims to JWTs allows you to share identity information without repeated queries to external data sources.
Read on to learn how to customize claims with SlashID's webhooks.

New Feature
/ 19 Feb, 2024SlashID: Building a globally distributed Identity Platform
We built the SlashID infrastructure so that your user data is globally distributed.
Our architecture helps applications using SlashID benefit from dramatically reduced latency, high availability and comply with data protection laws without fragmented identity silos or extra fees.


Deep Dives
/ 31 Jan, 2024Passkeys Adoption Trends: Survey from Large Deployments
In this comprehensive blog post, we delve into the publicly available data on large-scale passkeys rollouts, examining results, conversion rates, and implementation challenges as documented in engineering blogs by companies like Kayak and Yahoo Japan.

Security
/ 18 Jan, 2024Single Sign-On implementation: Safely retrieving the email claim
A number of security issues have been discovered recently caused by the reliance on the email claim when using OpenID Connect (OIDC) for SSO.
In this blog post we'll review some of the major OIDC providers to discuss how to retrieve the claim safely

Security
/ 8 Jan, 2024Single Sign-On implementation: Security Issues and Best Practices
Social logins and OpenID Connect (OIDC) are an extremely effective way to register new users with low friction.
There are many libraries out there that implement OIDC with several providers, however the implementation is very error-prone and can expose an application to account takeover attacks.
In this article, we’ll discuss the common security issues found in OAuth 2.0/OIDC login flows and best practices on how to avoid them.

New Feature
/ 2 Jan, 2024Introducing the SlashID Remix SDK: Authentication made easy
We’re excited to announce first-party Remix support in SlashID with @slashid/remix. We've borrowed the power of our React SDK and aligned it with Remix's unique design patterns.
The Remix SDK makes authentication for Remix easy and seamless.

Security
/ 27 Nov, 2023Firebase Authentication and Google Identity Platform User Enumeration Vulnerability
Firebase Authentication and Google Identity Platform are the two Google products that offer identity management.
Both products suffer from a vulnerability that allows an attacker to enumerate users on an application powered by Firebase Authentication or Google Identity Platform.
In this article, we’ll show how this vulnerability can be used and what the impact is.


New Feature
/ 27 Oct, 2023GDPR Compliance: Consent Management
Effortless GDPR compliance out of the box. Notify users about your intent to use cookies and request their consent.


