Blog
Security
/ 16 Jan, 2026Scattered Spider Tradecraft: Identity Abuse, Attack Flow, and Defense
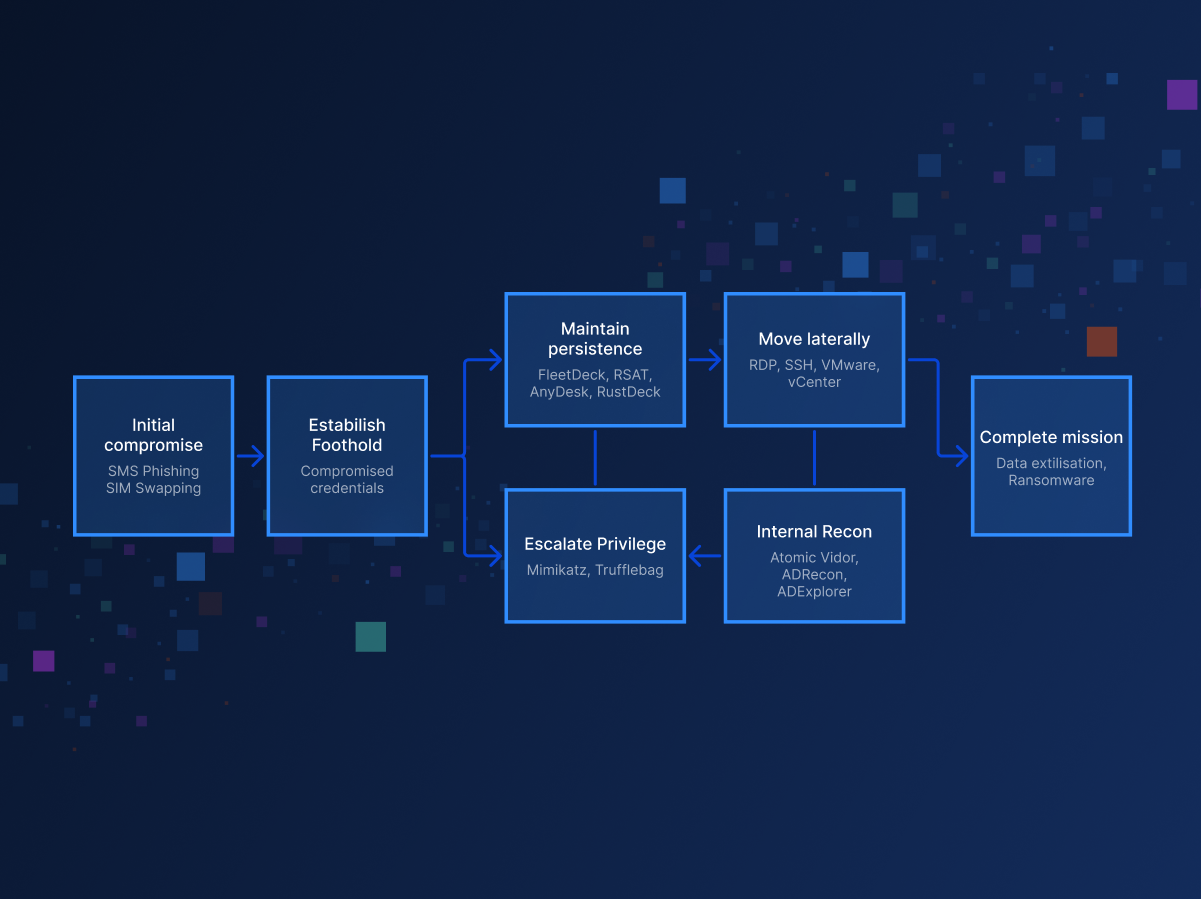
Scattered Spider is a highly adaptive cybercrime group that breaches enterprises by abusing identity, trust, and legitimate access paths rather than malware exploits.
Learn about their identity-centric attack flow, real-world campaigns like the MGM and Caesars breaches, and how to defend against these sophisticated threats.
Security
/ 16 Jan, 2026Scattered Spider Tradecraft: Identity Abuse, Attack Flow, and Defense
Scattered Spider is a highly adaptive cybercrime group that breaches enterprises by abusing identity, trust, and legitimate access paths rather than malware exploits.
Learn about their identity-centric attack flow, real-world campaigns like the MGM and Caesars breaches, and how to defend against these sophisticated threats.

Deep Dives
/ 22 Aug, 2024A deep dive in the AWS credential leaks reported by Palo Alto Networks
Thousands of credentials were exfiltrated from exposed .env files in the latest large-scale attack uncovered by Palo Alto.
Protecting cloud services and non-human identities spread across many vendors and environments is now table-stakes: SlashID can help.

New Feature
/ 22 Jul, 2024SlashID RBAC: Globally-available role-based access control
SlashID RBAC is a globally replicated role-based access control system that allows you to restrict access to resources based on permissions assigned to specific persons.
In this post, we will show you how to use RBAC in SlashID, and how to create permissions, and roles, and assign them to persons.

Security
/ 15 Jul, 2024Protecting against Snowflake breaches
In the last few weeks several very high-profile breaches have been in the news, from Santander to Ticketmaster and AT&T.
These breaches all have the same attack vector: identity-based attacks against Snowflake instances.
In this article, we discuss the causes of the breach and our approach to protect against identity-based attacks against Snowflake.

New Feature
/ 24 Jun, 2024Introducing the SlashID Local Deployment
The SlashID local deployment is our answer for developers looking to build, run and test apps locally.
Local development with SlashID can be a good fit for your evaluation, prototyping, development, and continuous integration workflows.


Security
/ 17 Jun, 2024ODPR: A Framework for Securing Non-Human Identities
Identity-based attacks have become the primary way attackers move laterally in a network. They are also responsible for half of the initial intrusions.
Addressing these attacks requires very different tooling and approaches compared to malware-based attacks.
In this article we delve into the SlashID framework to address these attacks.

New Feature
/ 10 Jun, 2024Credential Tokenization: Protecting third-party API credentials
Stolen secrets and credentials are one of the most common ways for attackers to move laterally and maintain persistence in cloud environments.
In this blog post we introduce credential tokenization to protect secrets at runtime, introduce separation of duties, and reduce the credential rotation burden.

New Feature
/ 3 Jun, 2024Secure API and M2M Access with OAuth2 Client Credentials and SlashID's sidecar
The recent Hugging Face breach is yet another reminder that securing machine-to-machine communication and API access is essential today.
By leveraging OAuth2 Client Credentials, you can enhance security, enable fine-grained access control, simplify credential management, and benefit from a standards-based approach.

New Feature
/ 14 May, 2024Introducing Organization Attributes
With organization attributes, you can now easily store and manage tenant-level data directly on our platform.

New Feature
/ 24 Apr, 2024Introducing Anonymous Users: Balancing First-Party Data Collection and User Experience
With the deprecation of third-party cookies, first-party data has become crucial for websites to personalize user experiences.
SlashID introduces Anonymous Users, a feature that allows websites to collect user data without forcing users to register or log in, striking the perfect balance between data collection and user experience.


