Blog
Security
/ 16 Jan, 2026Scattered Spider Tradecraft: Identity Abuse, Attack Flow, and Defense
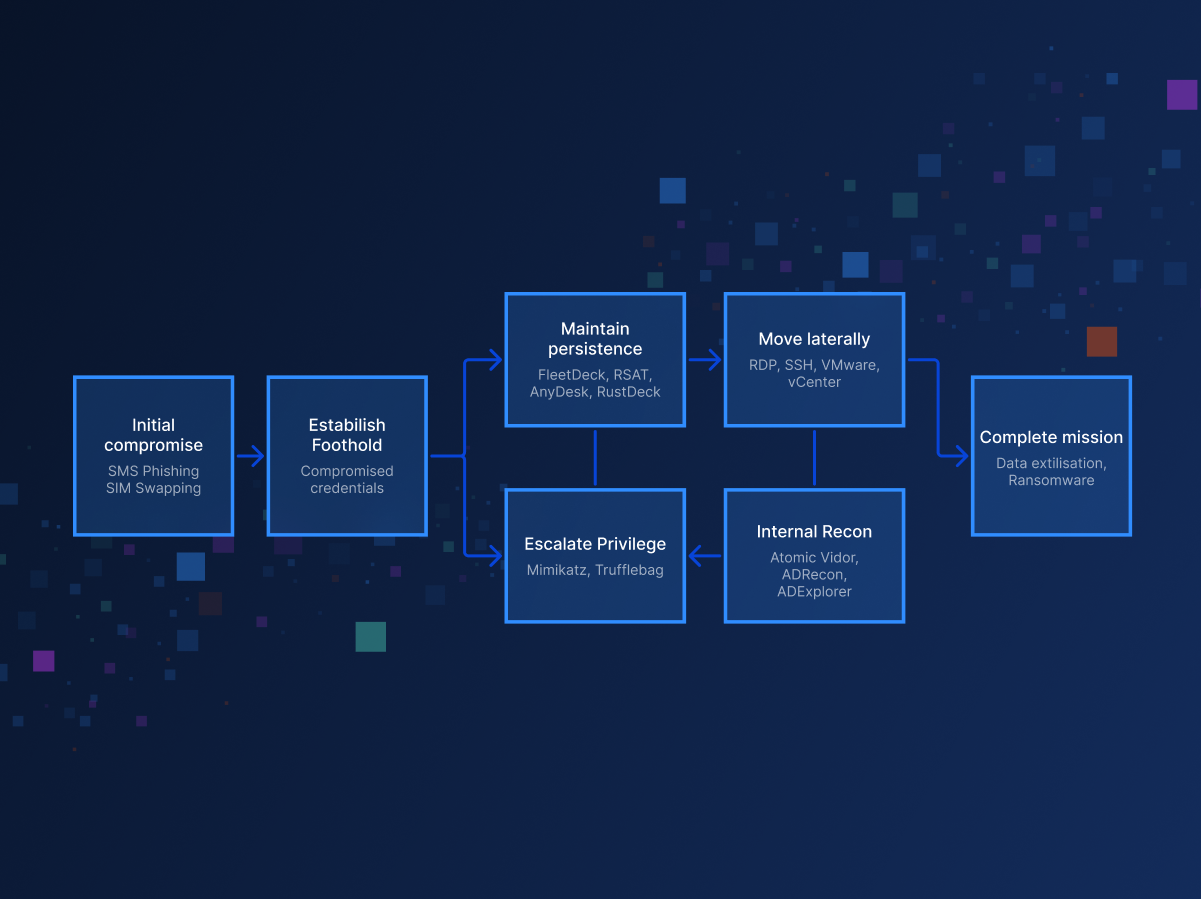
Scattered Spider is a highly adaptive cybercrime group that breaches enterprises by abusing identity, trust, and legitimate access paths rather than malware exploits.
Learn about their identity-centric attack flow, real-world campaigns like the MGM and Caesars breaches, and how to defend against these sophisticated threats.
Security
/ 16 Jan, 2026Scattered Spider Tradecraft: Identity Abuse, Attack Flow, and Defense
Scattered Spider is a highly adaptive cybercrime group that breaches enterprises by abusing identity, trust, and legitimate access paths rather than malware exploits.
Learn about their identity-centric attack flow, real-world campaigns like the MGM and Caesars breaches, and how to defend against these sophisticated threats.

Open Source
/ 28 Aug, 2023Docusaurus - Authentication and authorization with SlashID
The latest docusaurus-slashid-login theme adds finer grained access control to your Docusaurus website.

New Feature
/ 25 Jul, 2023Authenticate your Shopify customers with SlashID
The new SlashID Login app for Shopify lets your customers authenticate seamlessly using quick and safe methods like passkeys, social login and magic links.



New Feature
/ 20 Jul, 2023Synchronous Webhooks
We are excited to release synchronous webhooks, the latest addition to our webhooks features.
With synchronous webhooks, you can extend SlashID Access to suit your business needs in a few simple steps, in whatever language and environment makes sense for you.

Tutorial
/ 16 Jul, 2023Building a React Login Page Template
Discover how to create a secure login page for your React app with authentication and styling using SlashID.

New Feature
/ 10 Jun, 2023SlashID Analytics Webhooks
We are excited to release SlashID analytics and webhooks, providing greater visibility and actionable insights into your authentication flows.


Deep Dives
/ 24 May, 2023Passkeys - Threat modeling and implementation considerations
In this blog post, we review the current state of the technology from a security standpoint and we’ll discuss some critical aspects of passkey implementation.


New Feature
/ 12 May, 2023Authentication flows with SlashID
Implement MFA and Step-Up Authentication in React applications with SlashID.


Tutorial
/ 20 Feb, 2023Using Google Tink to sign JWTs with ECDSA
In this blog post, we will show how the Tink cryptography library can be used to create, sign, and verify JSON Web Tokens (JWTs), as well as to manage the cryptographic keys for doing so.

New Feature
/ 9 Feb, 2023React SDK support for <Groups>
With the latest React SDK release we are introducing a new control component, <Groups>. You can use <Groups> to conditionally render parts of the UI depending on whether the authenticated user belongs to specific Groups.



