Blog
Security
/ 16 Jan, 2026Scattered Spider Tradecraft: Identity Abuse, Attack Flow, and Defense
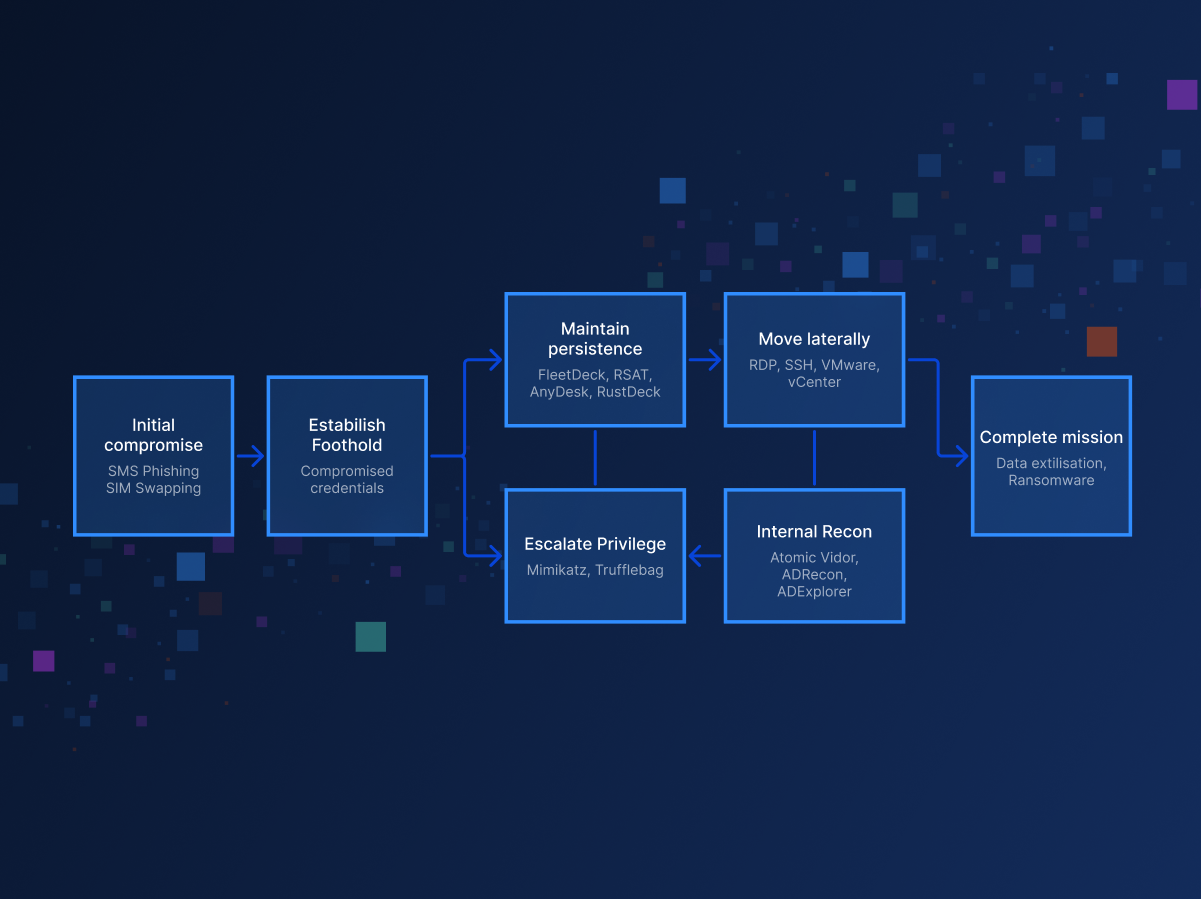
Scattered Spider is a highly adaptive cybercrime group that breaches enterprises by abusing identity, trust, and legitimate access paths rather than malware exploits.
Learn about their identity-centric attack flow, real-world campaigns like the MGM and Caesars breaches, and how to defend against these sophisticated threats.
Security
/ 16 Jan, 2026Scattered Spider Tradecraft: Identity Abuse, Attack Flow, and Defense
Scattered Spider is a highly adaptive cybercrime group that breaches enterprises by abusing identity, trust, and legitimate access paths rather than malware exploits.
Learn about their identity-centric attack flow, real-world campaigns like the MGM and Caesars breaches, and how to defend against these sophisticated threats.

New Feature
/ 18 Jan, 2023Sign-in and Sign-up React component release
Today we’re happy to announce the next step in that journey to deliver a streamlined, low friction onboarding experience to our customers with the release of our sign-up/sign-in form component.

New Feature
/ 16 Jan, 2023Fetching Google Groups with SlashID SSO
Use SlashID to fetch Google Groups as part of a user authentication flow.

Experiments
/ 18 Dec, 2022In-browser HSM-backed Encryption with Tink and Wasm
This post explores how to use Wasm to lift Tink to JavaScript and how you can leverage it to perform client-side encryption directly from the browser, backed with a master key stored in a HSM.

New Feature
/ 28 Nov, 2022Official React SDK release
Today we’re excited to announce the public release of the official SlashID React SDK
In this blog post we’ll go over the design pillars, main features, and why we’re thrilled about what’s coming next.

Open Source
/ 12 Nov, 2022Adding Identity to Docusaurus
Today we are releasing the docusaurus-slashid-login theme as well as a fork of docusaurus-openapi-docs.
The slashid plugin enables you to add out of the box authentication to docusaurus. The docusaurus-openapi-docs fork allows you to autofill API keys data, API parameters and more through slashid user attributes.


New Feature
/ 7 Nov, 2022Introducing Data Vault - Secure HSM-backed PII storage directly from the frontend
Today we are releasing Data Vault, which allows the safe and compliant storage of sensitive user data directly from the frontend.
Data Vault takes care of data localization and protection transparently, without having to build ad-hoc infrastructure to handle encryption or key management and rotation.


New Feature
/ 1 Nov, 2022Social logins in 5 minutes or less
Today we are releasing our OpenID Connect (OIDC) SSO module which you can use to add Social logins and OIDC-compatible SSO to your app in less than 5 minutes.
Social logins can significantly boost user registration - for instance, Pinterest reported a 47% registration increase after adding Google One Tap to their website.

Deep Dives
/ 20 Oct, 2022App-layer cryptographic primitives for secure storage of user data
In this blogpost we explore the cryptographic primitives and design decisions we made building our Data Vault module.
Our service is a globally replicated, field-level encrypted, data store to keep user data safe and compliant with Data Protection laws while improving UX by decreasing latency through data locality.


Deep Dives
/ 23 Sep, 2022The good, the bad and the ugly of Apple Passkeys
The widely anticipated Apple passkeys launch happened just a few weeks ago with the iOS 16 release.
Passkeys are a cross-device extension of FIDO credentials compatible with WebAuthn. They address the main UX issue of WebAuthn, cross-device credentials.
In this article we’ll explore the Apple passkeys implementation, how passkeys compare to traditional FIDO credentials and why the decision of Apple to get rid of device attestation and resident keys is a significant step back for security.


